In accordance with ITProPortal, the cybercrime economy could be bigger than Apple, Google and Facebook combined. The has matured into an prepared empire market that is probably more profitable compared to the drug trade. Criminals use impressive and state-of-the-art tools to grab data from large and small organizations and then sometimes put it to use themselves or, most frequent, provide it to other criminals through the Dark Web.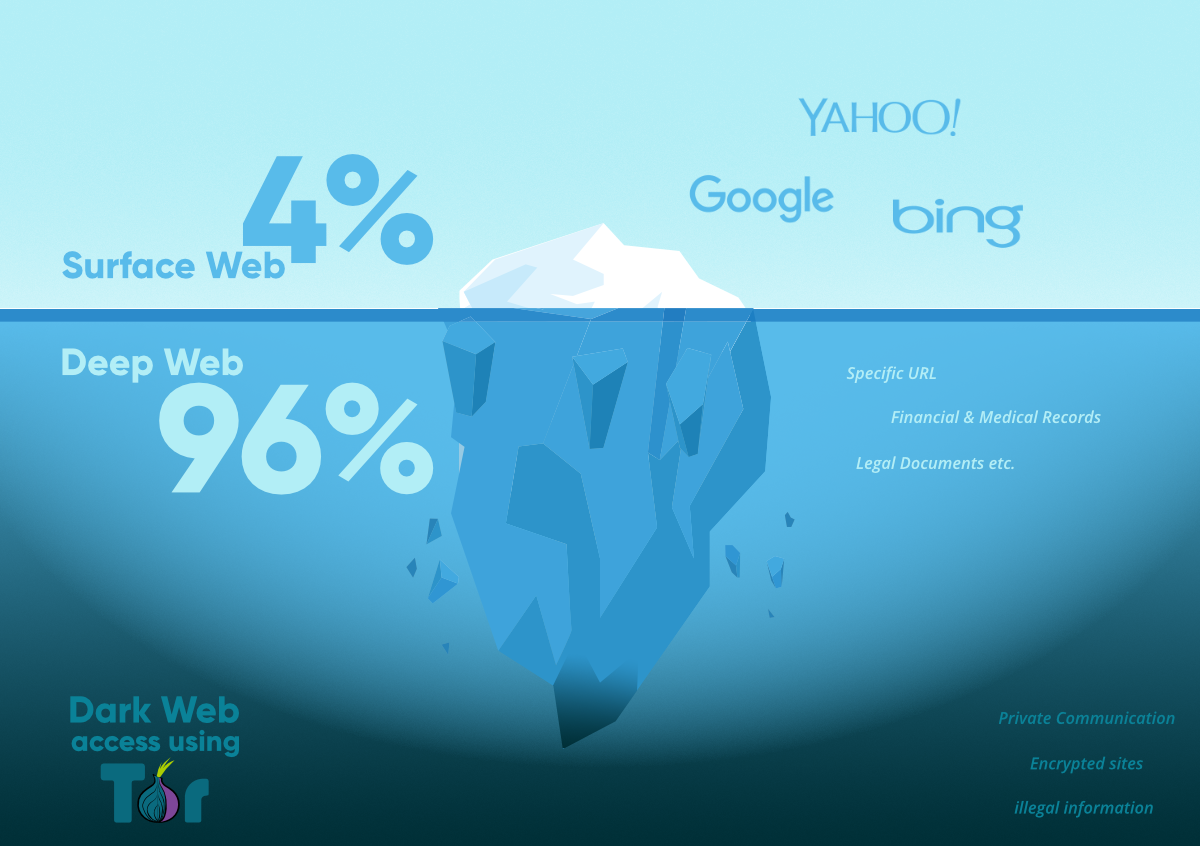
Little and mid-sized firms have end up being the goal of cybercrime and knowledge breaches because they do not have the interest, time or income to setup defenses to guard against an attack. Several have 1000s of accounts that hold Particular Determining Data, PII, or sensible property that’ll include patents, study and unpublished electric assets. Other little firms function right with bigger agencies and can offer as a site of entry significantly just like the HVAC company was in the Goal information breach.
A few of the smartest minds are suffering from innovative ways to avoid useful and individual data from being stolen. These data protection applications are, for the absolute most portion, defensive in nature. They fundamentally put up a wall of protection to keep spyware out and the info inside secure and secure.
Sophisticated hackers discover and use the organization’s lowest hyperlinks to setup an attack. However, even the very best defensive applications have holes inside their protection. Here would be the difficulties every organization people according to a Verizon Data Breach Investigation Record in 2013: 76 percent of system intrusions explore fragile or stolen credentials. 73 % of on line banking customers delete their accounts for non-financial websites. 80 percent of breaches that included hackers applied taken credentials. Symantec in 2014 estimated that 45 % of all attacks is detected by old-fashioned anti-virus meaning that 55 % of episodes go undetected. The result is anti-virus pc software and defensive security applications can not hold up. The crooks could previously be inside the organization’s walls.
Little and mid-sized firms may suffer considerably from a knowledge breach. Sixty per cent go out of organization inside a year of a data breach according to the National Cyber Protection Alliance 2013. Exactly what do an business do to safeguard it self from a knowledge breach? For many years I have advocated the implementation of “Most useful Techniques” to protect personal pinpointing data within the business. You will find basic practices every company should apply to meet up certain requirements of federal, state and business rules and regulations. I’m sorry to say not many little and mid-sized businesses match these standards.
The next stage is anything new that a lot of corporations and their techs have not heard about or executed to their defense programs. It requires checking the Dark Web. The Black Web keeps the secret to slowing down cybercrime. Cybercriminals freely industry stolen information on the Black Web. It holds a success of data that might adversely impact a corporations’current and potential clients. This really is where criminals head to buy-sell-trade stolen data. It is simple for fraudsters to gain access to taken data they should infiltrate business and conduct nefarious affairs. Just one information breach could set an business out of business.
Luckily, there are businesses that constantly monitor the Black Web for taken information 24-7, 365 times a year. Criminals openly reveal these details through talk areas, blogs, sites, bulletin boards, Peer-to-Peer communities and other black industry sites. They recognize data because it accesses offender command-and-control machines from numerous geographies that national IP addresses cannot access. The total amount of affected information gathered is incredible. Like:
Millions of affected qualifications and BIN card numbers are harvested every month. Approximately one million affected IP addresses are harvested every day. These details may stay on the Black Web for weeks, months or, sometimes, years before it is used. An company that watches for taken data can see nearly immediately when their taken data shows up. The next phase would be to take proactive action to completely clean up the stolen data and prevent, what can become, a information breach or organization identification theft. The info, primarily, becomes useless for the cybercriminal.
What can occur to cybercrime when many small and mid-sized firms take that Black Internet monitoring severely? The result on the criminal area of the Dark Web could possibly be massive when nearly all companies apply the program and make the most of the information. The goal is to render taken information useless as rapidly as possible. There will not be significantly effect on cybercrime till many small and mid-sized corporations implement this type of bad action. Cybercriminals are relying upon not many companies take practical action, but when by some miracle corporations wake up and get activity we’re able to see an important affect cybercrime.
